Security Operations

My ipset hash is full!? I'm using Ubuntu Server and I created a separate fail2ban jail that uses "iptables-ipset-proto6-allports" as their ban action (thus using ipset instead of iptables). However, today I seem to hit the limit: `stderr: 'ipset v7.15: Hash is full, cannot add more elements'`. This can be confirmed by running the ipset -t list command: ```sh Name: f2b-manual Type: hash:ip Revision: 5 Header: family inet hashsize 32768 maxelem 65536 timeout 0 bucketsize 12 initval 0xbc28aef1 Size in memory: 2605680 References: 1 Number of entries: 65571 ``` Where the 65571 entries exceeds the maxelem (65536). So what now?? Could I create a banlist in a txt file or something? I just want to ban some large tech corps: https://gitlab.melroy.org/-/snippets/619
I use FreeOTP+ which is supposed to be developed by people from the Fedora project and is protected by fingerprint on Pixel. I discovered that my 2FA was disabled on lemmy.world after I logged out and then logged back in a day later instead of just keeping the auth cookie active in Vanadium. Since 2FA is required to change settings, how was this accomplished and what can I do to ensure that it doesn't happen again?
The NGINX access.log of my VPS is showing a curiosity. Instead of a simple request like this... ``` "GET / HTTP/1.1" ``` ...regular requests are coming in that look like this `"\x03\x00\x00\x13\x0E\xE0\x00\x00\x00\x00\x00\x01\x00\x08\x00\x03\x00\x00\x00"` Is this some kind of hack attempt? Here's an example of a full line from the log... `15.204.204.182 - - [24/Apr/2024:15:59:47 +0000] "\x03\x00\x00\x13\x0E\xE0\x00\x00\x00\x00\x00\x01\x00\x08\x00\x03\x00\x00\x00" 400 166 "-" "-"` EDIT: For what it might be worth, most of these requests come in singularly, from different IP addresses. Once (that I've noticed) repeated attempts came in quickly from one specific IP.
Ghidra training classes from NSA::undefined
 tierzerosecurity.co.nz
tierzerosecurity.co.nz
An intro to automated evasion and compilation of .NET offensive tools::Information Security Services. Offensive Security, Penetration Testing, Mobile and Application, Purple Team, Red Team
Phrack #71: Call For Paper::Phrack staff website.
 jfrog.com
jfrog.com
Data Scientists Targeted by Malicious Hugging Face ML Models with Silent Backdoor::Is Hugging Face the target of model-based attacks? See a detailed explanation of the attack mechanism and what is required to identify real threats >
New Server Side Prototype Pollution Gadgets Scanner from Doyensec::Unveiling the Server-Side Prototype Pollution Gadgets Scanner
 tracebit.com
tracebit.com
It's now possible to find the AWS Account ID for any S3 Bucket (private or public)::A technique to find the Account ID of a private S3 bucket.
“SubdoMailing” — Thousands of Hijacked Major-Brand Subdomains Found Bombarding Users With Millions of Malicious Emails::undefined
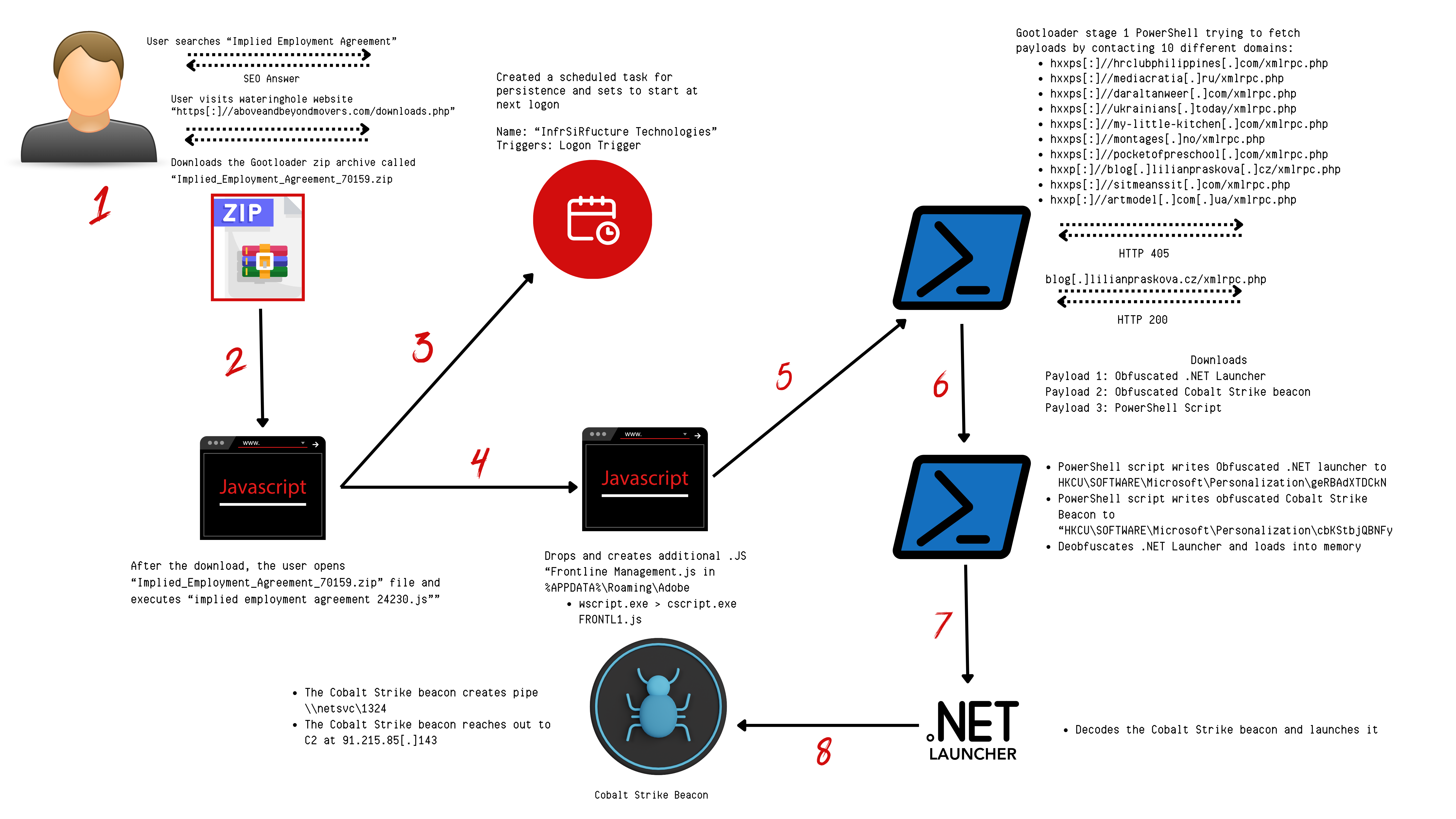 thedfirreport.com
thedfirreport.com
SEO Poisoning to Domain Control: The Gootloader Saga Continues::Key Takeaways More information about Gootloader can be found in the following reports: The DFIR Report, GootloaderSites, Mandiant, Red Canary, & Kroll. An audio version of this report can be … Read More
Code injection or backdoor: A new look at Ivanti's CVE-2021-44529::In 2021, Ivanti patched a vulnerability that they called “code injection”. Rumors say it was a backdoor in an open source project. Let’s find out what actually happened!
Python Risk Identification Tool for generative AI (PyRIT)::The Python Risk Identification Tool for generative AI (PyRIT) is an open access automation framework to empower security professionals and machine learning engineers to proactively find risks in their generative AI systems. - Azure/PyRIT
New TP-Link authentication Bypass!::undefined
Optum / Change Healthcare Breach::Optum Solutions's Status Page - Update: Some applications are experiencing connectivity issues..
 blog.phylum.io
blog.phylum.io
Ongoing Malware Laced Developer Job Interviews::Phylum continues to discover malware polluting open-source ecosystems. In this blog post, we take a deep-dive into an npm package trying to masquerade as code profiler which actually installs several malicious scripts including a cryptocurrency and credential stealer. Curiously, the attacker attempted to hide the malicious code in a test
Lockbit Ransomeware global taketown::With indictments and arrests.
GitHub - mlcsec/FormThief: Spoofing desktop login applications with WinForms and WPF::Spoofing desktop login applications with WinForms and WPF - mlcsec/FormThief
 blog.securelayer7.net
blog.securelayer7.net
Ivanti Connect Secure Under Attack: Uncovering Five Exploitable CVEs - XXE::Time and again, securing you
Analysis of Mirai variant leveraging CVE-2023-1389::undefined
 attackshipsonfi.re
attackshipsonfi.re
Exploiting Unsynchronised Clocks::TL;DR According to data from RIPE, over 40% of computers attached to the Internet have a few seconds of clock drift, which with the right combination of headers, will make an HTTP response unintentionally cacheable. Background Like many parts of the HTTP model, caching has been extended and revised multiple times over the years. The result is a confusing set of response header values, which affect the way that the browser may or may-not cache the response.
 www.aquasec.com
www.aquasec.com
Snap Trap: The Hidden Dangers Within Ubuntu's Package Suggestion System::Aqua Nautilus researchers have identified a security issue that arises from the interaction between Ubuntu’s command-not-found package and the snap package repository. While command-not-found serves as a convenient tool for suggesting installations for uninstalled commands, it can be inadvertently manipulated by attackers through the snap repository, leading to deceptive recommendations of malicious packages. Additionally, our …
 decoded.avast.io
decoded.avast.io
Decrypted: Rhysida Ransomware - "we are now publicly releasing our decryptor for download to all victims of the Rhysida ransomware"::The team at Avast has developed a decryptor for the Rhysida ransomware and released it for public download. The Rhysida ransomware has been active since May 2023. As of Feb 2024, their TOR site lists 78 attacked companies, including IT (Information Technology) sector, healthcare, universities, and government organizations.
 www.cyberark.com
www.cyberark.com
Breach Analysis: APT29’s Attack on Microsoft - Password Spray & OAuth abuse.::undefined
 www.troyhunt.com
www.troyhunt.com
Troy Hunt: How Spoutible’s Leaky API Spurted out a Deluge of Personal Data::Ever hear one of those stories where as it unravels, you lean in ever closer and mutter “No way! No way! NO WAY!” This one, as far as infosec stories go, had me leaning and muttering like never before. Here goes: Last week, someone reached out to me with what
JSON Smuggling: A far-fetched intrusion detection evasion technique::undefined
Shellcode evasion using Wasm/Wat and Rust::undefined
 archive.org
archive.org
ShmooCon 2024 Videos are up!::ShmooCon 2024by Shmoo Group, various presentersThe videos in this collection are from ShmooCon 2024, which occurred on 12 - 14 January 2024, at the Washington...
apk.sh makes reverse engineering Android apps easier, automating some repetitive tasks like pulling, decoding, rebuilding and patching an APK.::apk.sh makes reverse engineering Android apps easier, automating some repetitive tasks like pulling, decoding, rebuilding and patching an APK. - GitHub - ax/apk.sh: apk.sh makes reverse engineering Android apps easier, automating some repetitive tasks like pulling, decoding, rebuilding and patching an APK.
Trends in Phishing, Fraud, 'Dark AI Models', and how to better protect yourself.::We guard your domain, so you have peace of mind. Threat Visibility Platform.
Deluder: Python utility for intercepting traffic of applications. Deluder can be used as an alternative for EchoMirage. It supports OpenSSL, GnuTLS, SChannel, WinSock and Linux Sockets out of the b...::Deluder is a tool for intercepting traffic of proxy unaware applications. Currently, Deluder supports OpenSSL, GnuTLS, SChannel, WinSock and Linux Sockets out of the box. ⚡ - GitHub - Warxim/deluder: Deluder is a tool for intercepting traffic of proxy unaware applications. Currently, Deluder supports OpenSSL, GnuTLS, SChannel, WinSock and Linux Sockets out of the box. ⚡
AnyDesk Incident Response 2-2-2024::undefined
Your Security Program Is Shit::Very shit
Frog4Shell — FritzFrog Botnet Adds One-Days to Its Arsenal::undefined
 snyk.io
snyk.io
Leaky Vessels: Docker and runc Container Breakout Vulnerabilities - January 2024::Snyk Security Labs Team has identified four container breakout vulnerabilities in core container infrastructure components including Docker and runc, which also impacts Kubernetes.
CVE-2023-6246: Heap-based buffer overflow in the glibc's syslog()::undefined
New Visual Studio Code plugin for IaC security (plus collaboration, semgrep integration)::Introducing PoIEx - Points Of Intersection Explorer


